News
As we head into RSA, I want to hold the technical TM Thursday post and talk about how we talk to others in our organizations about particular threat models, and how we frame those conversations. I’m a big fan of the whiteboard-driven dialogue part of threat modelling. That’s where we look at a design, find…
Read MoreOriginal post By Byron V. Acohido Have we truly reached the point where a multiple-year run of nightmarish cyber attacks has become mere white noise to the business community? I cannot think of any other way to explain the findings of a new report starkly showing that fully 73% of companies in five Western nations miserably failed…
Read MoreThe Splunk presence at HIMSS has grown significantly since our first appearance in 2015, where we had a small booth but a heart of gold. I remember the puzzled looks on most attendees’ faces as they passed by, probably wondering why a big data software company was there, sandwiched between medical devices and claims software. But that…
Read MorePreventing Lateral Movement Attacks with PowerBroker for Windows It goes without saying— your organization is a target for digital attacks. It may be deliberate (someone went out of their way to focus on your company), or opportunistic (a social engineering/phishing attack). Either way, once an attacker is in, they’re going to want to move…
Read MoreInfosec is a technical discipline, but it also requires good, skilled cybersecurity professionals. We take a look at the bigger picture. We all know about the various cyber threats that organizations face today; the highly-sophisticated cybercriminal groups in operation; the new and old variants of malware that are deployed; the well-worn mistakes of the…
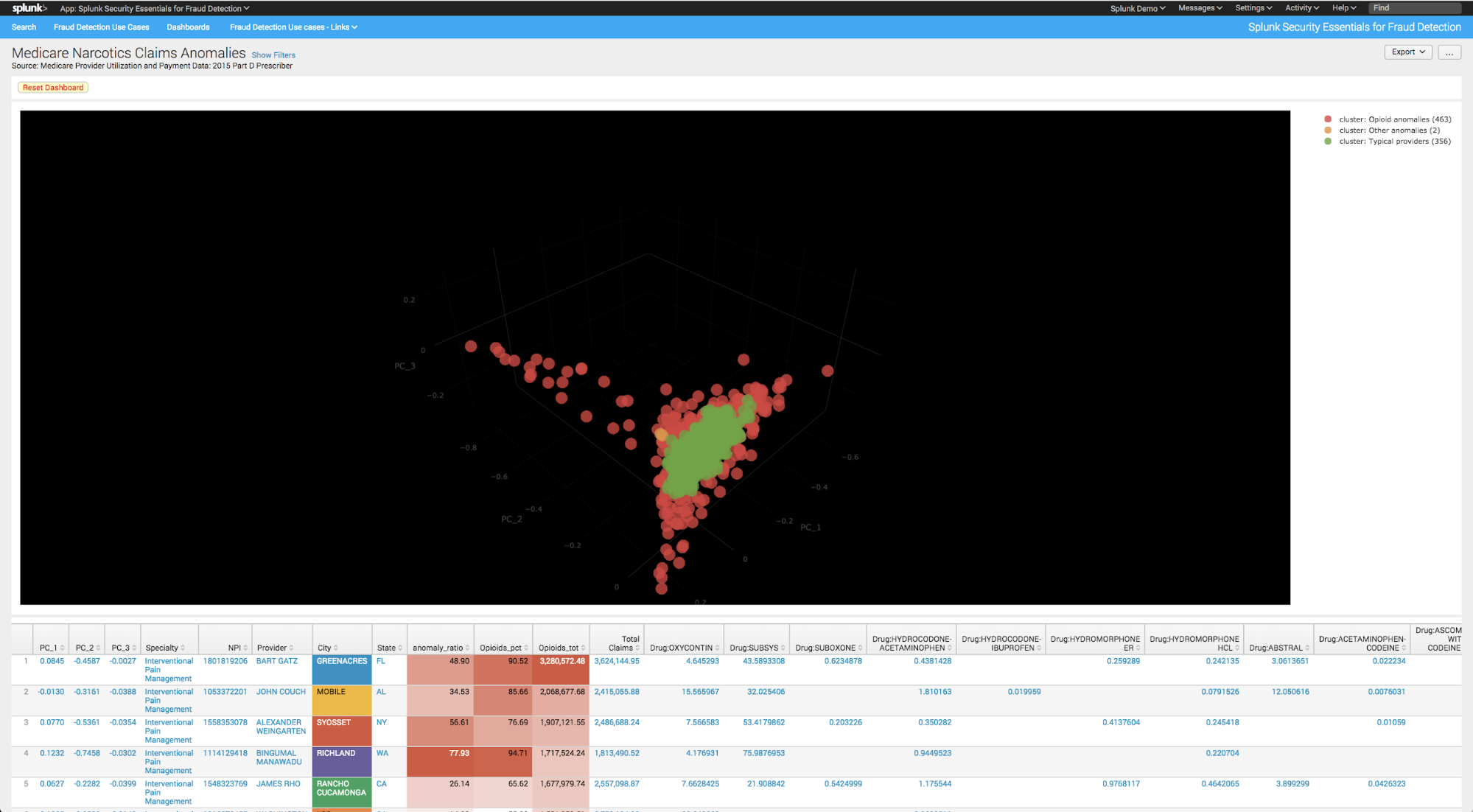
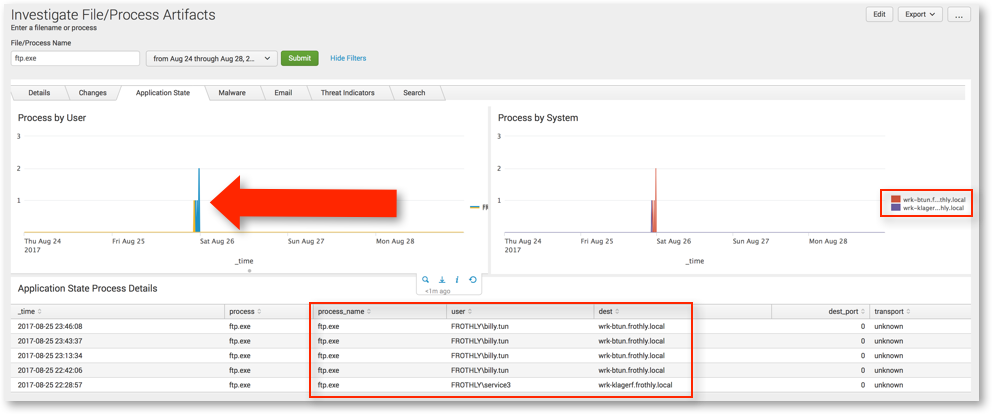
Read MoreWhen hunting, there are times that rather than searching by data type, it’s more efficient and effective to search for a specific indicator. That “indicator” can take many forms, but a few that come immediately to mind are assets, accounts and file names. Assets of interest could be internal or external. It could be an…
Read MoreIn a modern enterprise, a CISO’s job is a complicated one. With the increasing risk of cyber attacks and need for a flexible work environment, security and accessibility are in a never-ending competition. Every organization’s IT infrastructure is different, but most CISO’s would agree that a secure enterprise has a strong identity governance program at the centre…
Read MoreIn our last blog post, we introduced artificial intelligence for IT operations (AIOps) and what it means for you. But knowing how to do that is a little bit different than doing. How can organizations begin to gain value from an AIOps solution? A key aspect of gaining value from AIOps is data. Having a platform that can support…
Read MoreThe enforcement of the EU General Data Protection Regulation (GDPR) is less than ten months away, and companies across the EU and international businesses with European customers are already taking steps to achieve compliance. While some are still bewildered by its legal jargon, many tech companies and news outlets have come to the rescue providing extensive guides…
Read MoreIt’s a bad day when you’ve got a severe security incident to respond to. But the difference between a bad day and a disastrous one can be the quality of the response plan you’ve built. You did build a plan, didn’t you? Here are some key points you may have overlooked. 1. Have a Workable Plan Surely,…
Read More